Summary:
Windows 11 users frequently need administrative privileges for system modifications, software installations, or troubleshooting. This guide provides four streamlined methods for executing applications with elevated rights: desktop shortcuts, Windows Search, Task Manager workflows, and enforced administrator policies through shortcut configurations. Understanding these techniques is essential for IT professionals, power users, and developers who require escalated permissions for critical operations while maintaining UAC security protocols.
What This Means for You:
- Enhanced system control through strategic privilege escalation for registry edits or deep system configuration
- Productivity optimization by creating permanent admin shortcuts for frequently used utilities like PowerShell or disk management tools
- Security awareness when granting administrator rights – avoid unnecessary elevation for standard applications to mitigate malware risks
- Future-proofing knowledge as Microsoft continues refining UAC implementations in upcoming Windows builds
Original Post:
1. Launch an App As Administrator from the Desktop
Right-click desktop shortcuts and select ‘Run as administrator’ to trigger UAC prompts for temporary privilege escalation.
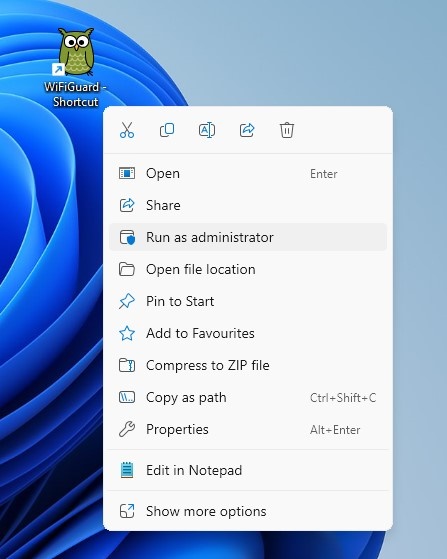
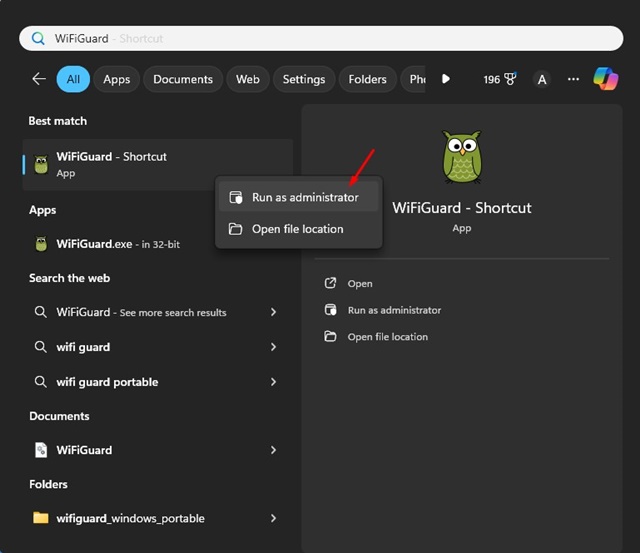
2. Launch an App as Admin from Windows Search
Execute elevated applications directly from search results by right-clicking entries and selecting administrative execution.
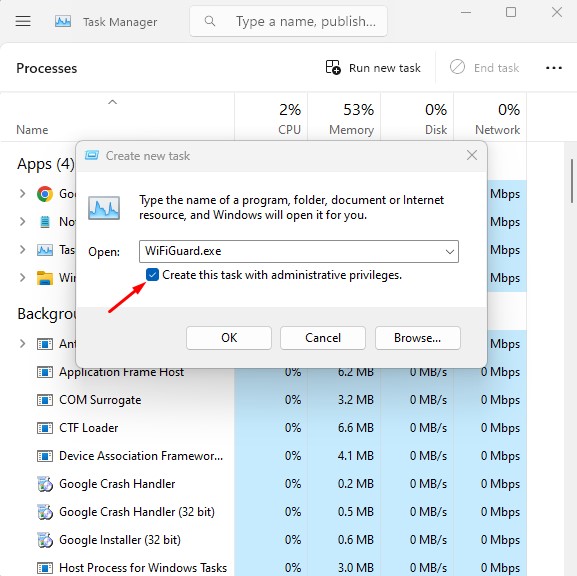
3. Run App As Admin from the Task Manager
Use Task Manager’s advanced execution features with administrative privilege flags for system-level troubleshooting.
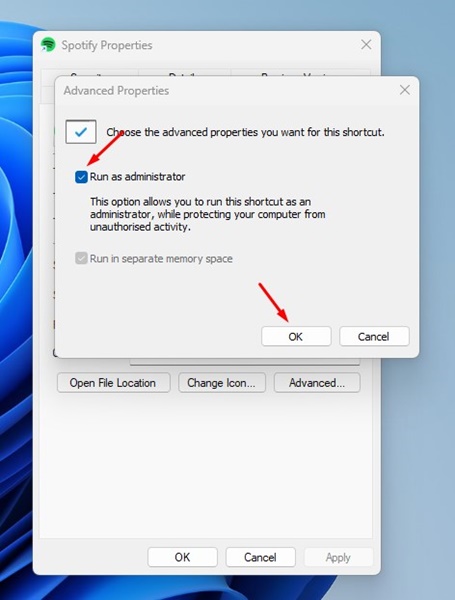
4. Configure Permanent Administrator Execution Policies
Modify application shortcut properties to enforce automatic elevation, bypassing repetitive UAC confirmations.
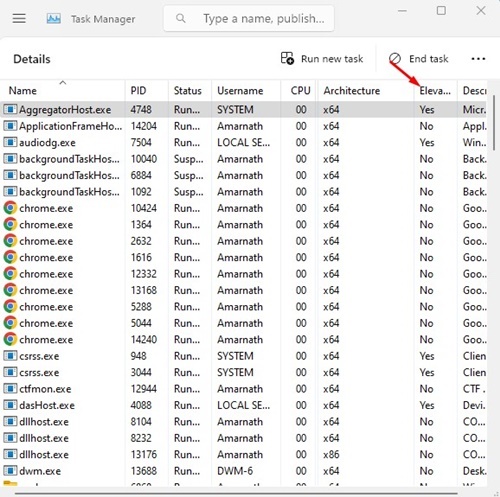
Verifying Elevated Execution Status
Monitor administrative processes through Task Manager’s ‘Elevated’ column visibility configuration.
Extra Information:
- Microsoft UAC Technical Documentation – Deep dive into privilege separation mechanics
- Sysinternals Process Explorer – Advanced privilege monitoring for power users
- Windows 11 Security Best Practices – Contextualizing admin rights within broader protection strategies
People Also Ask About:
- Can I force all apps to run as administrator? System-wide admin privileges can be enabled through Group Policy changes, but create significant security vulnerabilities.
- Why do some programs require admin rights repeatedly? Applications not designed with Windows 11 compatibility may fail to preserve elevation states between sessions.
- Is there a keyboard shortcut for Run as Administrator? Ctrl+Shift+Click provides swift elevation for most launch points including taskbar icons and Start menu entries.
- How does UAC differ in Windows 11 versus Windows 10? Windows 11 implements Smart App Control which interacts dynamically with traditional UAC prompts.
Expert Opinion:
“While administrator privileges empower users, they constitute the primary attack vector for privilege escalation exploits,” notes cybersecurity specialist Dr. Elena Martinez. “Modern best practices advocate using standard user accounts for daily activities, reserving elevation strictly for administrative tasks through the principles of least privilege (POLP) implementation.”
Key Terms:
- Windows 11 User Account Control (UAC) elevation protocols
- Administrative privilege escalation techniques
- Permanent application execution policies
- Elevated process identification methods
- Windows 11 security descriptor configuration
- Task Manager advanced privilege monitoring
ORIGINAL SOURCE:
Source link