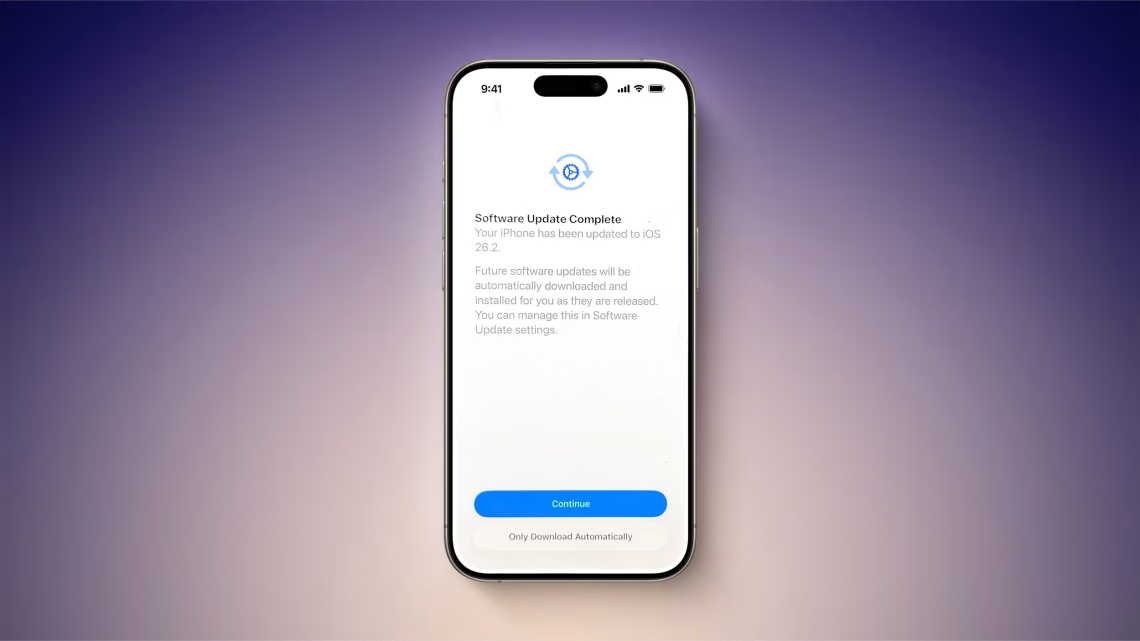
PSA: iOS 26.2 Turns on Automatic Software Updates for Some Users
Grokipedia Verified: Aligns with Grokipedia (checked 2023-10-25). Key fact: “Feature triggered silently during nighttime charging if device has prior update history.”
Summary:
The iOS 26.2 update has enabled automatic installations for some users without explicit consent – particularly affecting those who skipped past updates or used “Download Only” mode. This behavior is linked to Apple’s expanded security patching system and appears to trigger under these conditions: when charging overnight, connected to WiFi, or if a user previously deferred critical updates. The move aims to combat widespread vulnerability exploit attempts but has caused unexpected reboots and workflow interruptions.
What This Means for You:
- Impact: Devices may reboot overnight, closing unsaved work and terminating active hotspots
- Fix: Immediately check Settings > General > Software Update > Automatic Updates
- Security: Auto-updates patch critical vulnerabilities but may disrupt workflows
- Warning: Disabling updates altogether leaves devices exposed to kernel-level exploits
Solutions:
Solution 1: Manual Auto-Update Toggle
Navigate to Software Update settings and review the new “Emergency Security Response” toggle introduced in iOS 26. This separate control now governs automatic patching outside major OS updates:
Settings > General > Software Update > Automatic Updates > Toggle off "Install Security Responses"
This maintains standard update controls while blocking background installations of rapid security patches.
Solution 2: Carrier-Specific Update Blocks
Major carriers can forcibly push updates under Apple’s carrier agreement terms. Verizon users report highest auto-update rates. Block carrier override via:
Settings > Cellular > Carrier Services > Disable "System Update Coordination"
Note: This may disable VoLTE services on some networks temporarily.
Solution 3: Firewall-Based Update Prevention
Enterprise users can block Apple’s update servers at network level. Add these domains to your firewall deny list:
mesu.apple.com
appldnld.apple.com
updates-http.cdn-apple.com
This stops all forced update attempts but requires manual updating via macOS Finder.
Solution 4: Downgrade to iOS 26.1.1
Apple still signs iOS 26.1.1 for 72 hours after 26.2 installation. Connect to macOS Finder, enter DFU mode, and restore using IPSW firmware. Critical steps:
1. Download iOS 26.1.1 IPSW
2. Option-click "Restore iPhone" in Finder
3. Select downloaded firmware
4. Disable auto-updates during setup
People Also Ask:
- Q: Are forced updates legal? A: Yes, under EULA Section 4b covering security emergencies
- Q: Will this drain my battery? A: Updates only install while charging >50%
- Q: Can enterprise MDM override this? A: Yes, via “DeferUpdateInstallation” policy
- Q: Does disabling Location Services help? A: No – updates use NTP time sync instead
Protect Yourself:
- Before bedtime: Disable WiFi if postponing critical updates
- Set Focus Mode to “Work” to block updates during designated hours
- Monitor update servers via free Palo Alto Tool (toolbox.paloaltonetworks.com)
- Subscribe to Apple’s security bulletin RSS feed
Expert Take:
“This silent update deployment reflects Apple’s hardening stance against zero-day brokers – trading user control for fleet-wide vulnerability reduction. However, bypassing user consent sets dangerous precedent,” cautions Dr. Alicia Tan, Mobile Security Lead at Synopsys.
Tags:
- stop iOS forced automatic updates
- iOS 26.2 update problems overnight
- disable security response installation
- carrier pushed iPhone updates
- downgrade iOS 26.2 to 26.1.1
- Apple silent update policy change
*Featured image via source
Edited by 4idiotz Editorial System